Bybit hacker moves 62,200 ETH, full amount could be cleared in 3 days
The Lazarus group of North Korea has intensified efforts to whiten the funds of Bybit following what is considered to be the greatest piracy of cryptography in history with $ 1.4 billion.
The cyber attacks moved 62,200 ETH additional ($ 138 million) on March 1. This leaves them only 156,500 Ethereum (Ethn) Stay from the original flight, according to an analysis of the Crypto Embercn researcher.
The last transfer brings the total laundered amount to around 343,000 ETH, or almost 68.7% of the 499,000 ETH stolen during the attack on February 21. Based on the current rhythm, EMBCN provides that the pirates will erase the remaining funds in the next three days.
It accelerated whitening comes despite a recent intervention by the Federal Bureau of Investigation (FBI). The FBI officially attributed the hacking of $ 1.5 billion to North Korea in a public service announcement on February 26.
The FBI confirms North Korean responsibility
According to the FBI announcement, North Korea was responsible for the flight of approximately 1.5 billion dollars in virtual assets to the exchange of cryptocurrency by or around February 21, 2025.
The FBI has appointed this specific North Korean cyber-operation as a “traderra”.
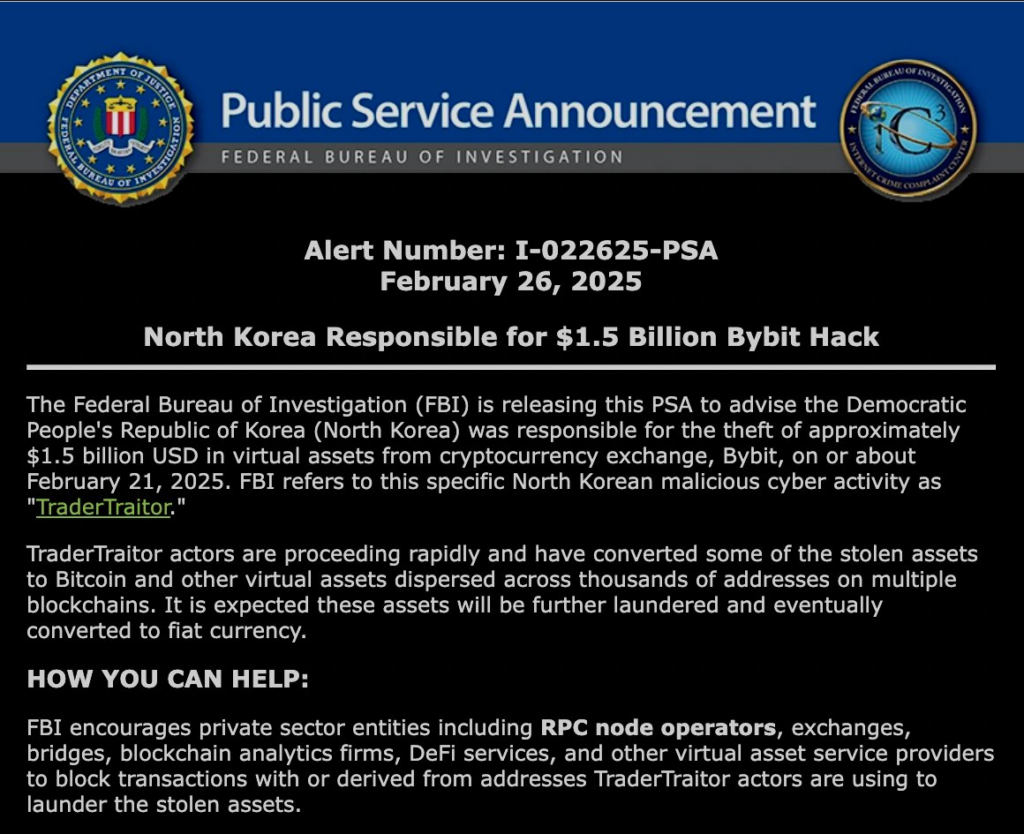
The announcement details that the actors of Trader will move quickly, having already converted parts of the active stolen into Bitcoin and other cryptocurrencies dispersed on thousands of addresses on several blockchains.
FBI officials expect these assets to be even more bleached and ultimately converted into fiduciary currency.
The FBI actively calls for the help of the private sector. They also asked RPC nodes operators, scholarships, bridges, blockchain analysis companies, DEFI services and other virtual asset service providers to block connected transactions to address traderaor active active active active ingredients.
The FBI shared addresses related to pirates, while the Blockchain Elliptic analysis company has widened surveillance efforts by signaling more than 11,000 portfolio addresses potentially linked to the operation.
According to Chainalysis, the pirates used various mixing techniques to hide the track of stolen funds. They also converted parts of Eth to Bitcoin (BTC), Stablecoin dai and other active ingredients.
The group mainly used decentralized exchanges, transversal bridges and instant exchange services without knowing your client’s requirements (KYC).













Post Comment