Hackers exploit SourceForge to hide crypto miners in Microsoft Office packages
Cybercriminals abuse the fields of the Sourceforge project to spread integrated trojanized office installers with cryptocurrency extraction tools and clippiper hackers.
A newly discovered malware campaign transforms the sourceforge infrastructure into a launch for infection, taking advantage of the friendly platform tools to encourage users to download malware cryptography software.
According to researchers from Kaspersky, the program targets Crypto users by disguising malicious software such as downloads linked to the office – with swollen installers, password protected archives and obscuscation layers that end up offering a crypto minor And a clipbanker to divert Crypto transactions.
In a blog article on Tuesday, April 8, the researchers said that the attackers had set up a false project on Sourceforge called “Officepackage”, designed to resemble Microsoft Office Copied supplements of Github. Although the project page itself may seem normal, the real trap was its sub-domain automatically generated “Officepackage.sourceforge.io”, noted the researchers. Search engines like RussiaThe Yandex recovered it, and when the users visited the page, they saw a false list of desktop applications with download buttons that really started infection of malware.
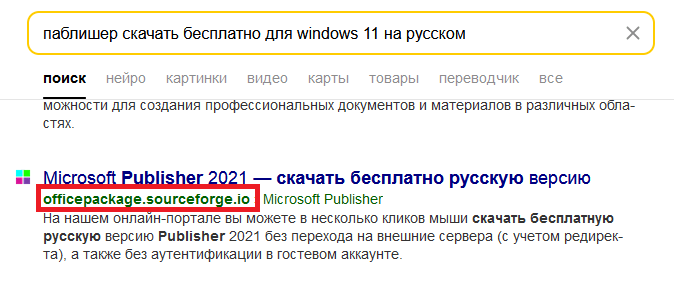
Click on false download links Sends users via several redirects before delivering a small zip file. But once a discharge, it develops in an inflated installation program of 700 MB.
When launched, the installer uses hidden scripts to enter more github files, finally unpack the malware that checks the antivirus tools before execution. If no threat is detected, it installs tools like Autoit and Netcat – a script sends system information to a Telegram Bot, while another guarantees that malware in cryptocurrency remain on the system, according to the researchers.
Kaspersky says that 90% of affected users seem to be in Russia, with more than 4,600 strokes between January and March. While the campaign mainly aims to fly cryptography funds, researchers warn that infected machines can also be sold to other threat actors.













Post Comment